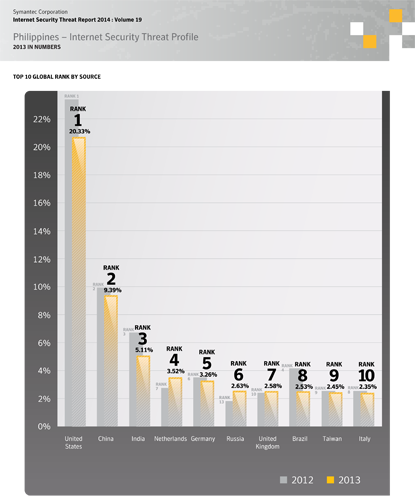
Security expert Symantec recently released its Internet Security Threat Report (ISTR) for 2013, which ranked the Philippines as 32nd among countries where Internet Security threat activities were rampant.
The Symantec report also shows a significant shift in cybercriminal behavior, revealing the bad guys are plotting for months before pulling off huge heists – instead of executing quick hits with smaller rewards.
“There has been a decline in Philippines’ cyber security threat profile, ranked 32nd globally last year. A key observation is while the level of sophistication continues to grow among attackers, what was surprising was their willingness to be a lot more patient – waiting to strike until the reward is bigger and better,” said Luichi Robles, Senior Country Manager, Symantec Philippines.
In 2013, there was a 62 percent increase in the number of data breaches from the previous year, resulting in more than 552 million identities exposed.
Each of the eight top data breaches in 2013 resulted in the loss of tens of millions of data records. By comparison, 2012 only had a single data breach reach that threshold.
Targeted attacks were up 91 percent and lasted an average of three times longer compared to 2012.
Personal assistants and those working in public relations were the two most targeted professions – cybercriminals use them as a stepping stone toward higher-profile targets like celebrities or business executives.
Symantec provided the following steps to help companies and individuals counter cyber threats and attacks:
For Businesses:
1. Know your data: Protection must focus on the information – not the device or data center. Understand where your sensitive data resides and where it is flowing to help identify the best policies and procedures to protect it.
2. Educate employees: Provide guidance on information protection, including company policies and procedures for protecting sensitive data on personal and corporate devices.
3. Implement a strong security posture: Strengthen your security infrastructure with data loss prevention, network security, endpoint security, encryption, strong authentication and defensive measures, including reputation-based technologies.
For Consumers:
1. Be security savvy: Passwords are the keys to your kingdom. Use password management software to create strong, unique passwords for each site you visit and keep your devices – including smartphones – updated with the latest security software.
2. Be vigilant: Review bank and credit card statements for irregularities, be cautious when handling unsolicited or unexpected emails and be wary of online offers that seem too good to be true – they usually are.
3. Know who you work with: Familiarize yourself with policies from retailers and online services that may request your banking or personal information. As a best practice, visit the company’s official website directly (as opposed to clicking on an emailed link) if you must share sensitive information.